Cutting-Edge BQT Biometrics Australia for Enhanced Security and Safety And Security
Maximizing Company Defense: The Ultimate Guide to Electronic Protection Solutions
In the hectic and ever-evolving landscape of company security, the dependence on digital safety and security solutions has actually come to be vital for securing important assets, personal info, and preserving operational continuity. In this overview to electronic security options, we will discover the most current trends, sophisticated modern technologies, and finest methods to fortify your business versus prospective threats and susceptabilities.
Value of Electronic Safety And Security Solutions
When considering the security of assets and delicate details, the significance of electronic protection options can not be overstated. In today's interconnected globe, where cyber dangers are continuously evolving and coming to be more sophisticated, companies must focus on carrying out durable digital protection procedures to safeguard their information and operations. Electronic safety remedies encompass a wide variety of innovations and practices created to resist unauthorized gain access to, information breaches, malware, and other cyber threats.
One of the vital advantages of electronic security options is their ability to give real-time monitoring and threat detection. BQT Electronic Security. Via devices like breach discovery systems, firewalls, and security information and event administration (SIEM) systems, companies can proactively recognize and react to security incidents prior to they escalate into major breaches. Furthermore, electronic safety options aid guarantee conformity with market guidelines and standards, securing businesses from prospective lawful and economic repercussions
Kinds Of Electronic Security Equipments
Offered the critical value of digital safety options in safeguarding companies against cyber risks, it is vital to explore the various kinds of digital safety systems available to enhance protection and durability. One of the most common kinds of electronic safety and security systems is the firewall software, which functions as an obstacle in between a firm's interior network and exterior networks, removing possibly damaging information. Invasion Detection Systems (IDS) are additionally important, as they keep track of network traffic for questionable activity and alert managers to potential risks. Furthermore, companies commonly depend on security technologies to secure sensitive information both at remainder and in transit. Gain access to control systems, consisting of biometric viewers and keycard access, assistance control access to physical rooms and secure possessions. Video clip security systems play a role in monitoring and recording activities within and around the facilities. By using a mix of these digital safety and security systems, services can develop a durable defense against different safety hazards.
Carrying Out Accessibility Control Steps

Additionally, accessibility control steps can be integrated with security systems to monitor and tape-record people' activities within secured areas. This combination boosts security by straight from the source offering a detailed review of who is accessing details places at any type of offered time. Access control systems can be configured to restrict accessibility based on time, area, or specific credentials, allowing businesses to customize security protocols according to their specific demands.
Cybersecurity Best Practices
To improve general safety pose, executing robust cybersecurity best practices is imperative in protecting digital assets and information honesty. One essential method is ensuring normal software program updates throughout all devices and systems to patch susceptabilities immediately. Employing solid, unique passwords and implementing multi-factor verification adds layers of protection versus unauthorized accessibility. Performing regular safety audits and assessments aids determine weaknesses and locations for enhancement. Employee training on cybersecurity awareness is critical in stopping social engineering strikes and guaranteeing a security-conscious labor force.
Establishing a detailed incident action plan enables swift and reliable reactions to protection breaches, lessening possible damage. Encrypting sensitive information both en route and at rest gives an additional barrier against information breaches. Applying access controls based on the concept of the very least privilege limits the direct best site exposure of crucial systems and details to just those who require it for their functions. Normal back-ups of data make certain that in the event of a ransomware attack or data loss, important details can be recovered. Embracing a positive strategy to cybersecurity through continuous tracking and danger knowledge aids detect and minimize potential risks before they escalate. By incorporating these finest methods right into cybersecurity methods, businesses can fortify their defenses against evolving cyber threats.
Security and Tracking Solutions
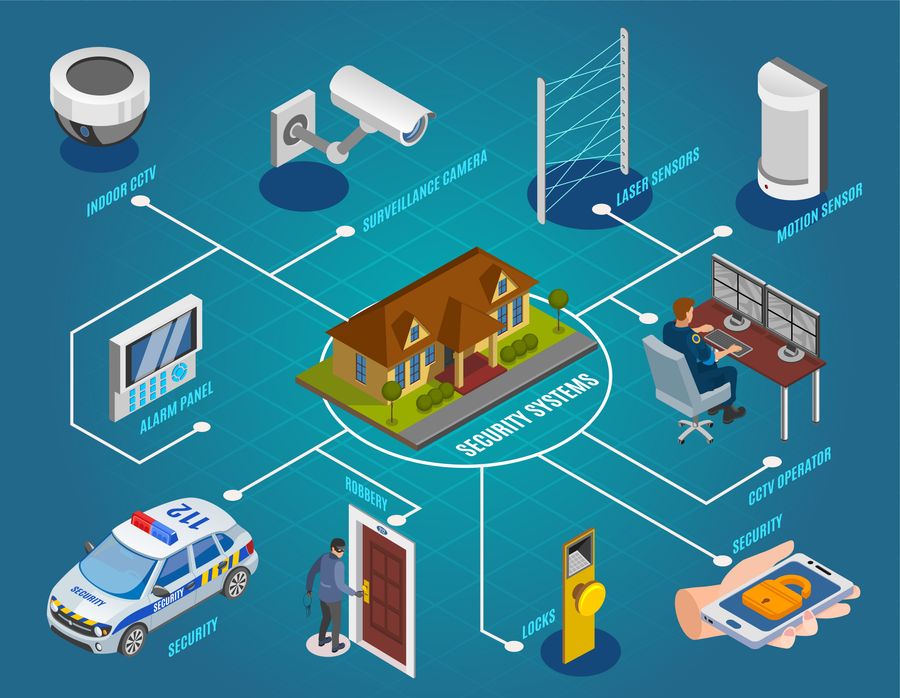
Video monitoring solutions use remote surveillance capabilities, enabling authorized employees to keep an eye on the facilities also when off-site. Additionally, advanced attributes like motion detection, face recognition, and certificate plate acknowledgment enhance the general protection posture of the organization. Integrating security systems with alarm systems and gain access to control better strengthens the safety and security facilities, making it possible for an aggressive action to potential safety and security breaches.
Final Thought
In verdict, digital safety and security remedies are crucial for making best use of organization security. It is essential to invest in the appropriate electronic protection systems to make sure the security and security of the company.